“Fullz is the treasure trove,” said John Shier, security advisor at Sophos. In our digital world, our personal information holds immense value. You may surprise to know big IT companies like Meta, google is making millions and billions by using your data even after providing completely free services, because knowingly unknowingly you have provided permission to them to use your data. But there are a lot of people out there who gather data without your permission and sell it over the dark web to make money. That complete set of your personal information is known as Fullz. Here we are going to explain all about Fullz, how it can harm you, how you can defend yourself against it, and many more.

1. What is Fullz?
Fullz or Fulls is a slang term used to describe a complete set of personal information belonging to someone.
It includes name, address, date of birth, social security number, bank account details, credit card information, and even online account usernames and passwords.

Cybercriminals gather this information from various sources, like when companies get hacked or through phishing scams.
1.2 What are The Types of Fullz?
Let’s explore together the different types of Fullz in simple terms:
1.2.1. Basic Fullz:
Basic Fullz typically includes basic information about a person, such as name, address, and phone number.
While this may not seem like much, cybercriminals can still use this information to launch phishing attacks or attempt social engineering techniques to extract further details.
1.2.2. Financial Fullz:
Financial Fullz contains additional financial information about an individual, including credit card numbers, bank account details, and routing numbers.
With this information, cybercriminals can attempt to make fraudulent transactions or even drain victims’ bank accounts.
1.2.3. Identity Fullz:
Identity Fullz provides a comprehensive package of personal information, often including a person’s full name, date of birth, social security number, and driver’s license details.
Armed with this data, cybercriminals can impersonate the victim, open new accounts, or apply for loans and credit cards in their name.
1.2.4. Online Fullz:
Online Fullz focuses on an individual’s online presence. This includes email addresses, usernames, and passwords for various online accounts.
Cybercriminals can use this information to gain unauthorized access to victims’ social media accounts, online shopping profiles, or even online banking platforms.
1.2.5. Medical Fullz:
Medical Fullz contains sensitive health-related information, such as insurance details, medical history, and social security numbers linked to healthcare records.
Criminals can exploit this data for insurance fraud or even sell it to unscrupulous parties for illegal medical activities.
👉 Read More: Credit Card Dump: Unveiling the Dark Side of Financial Fraud 🔥
1.3 What is Dead ☠ Fullz?
Dead Fullz is essentially data packages that have lost their validity as a result of a change in one or more key pieces of information.
This may occur on purpose, when the victim is aware that their credentials and personal information have been stolen, or it may occur unintentionally, such as when a person passes away.
Dead fullz can no longer be used for the majority of exploits; while they might momentarily function, even the most basic anti-fraud procedures will detect the attempt and reject it. These are still helpful, though, for some purposes, such as starting bank drop activities with specific banks.
✍ Key Learning :
- ✅ Fullz refers to a complete set of personal information, including names, addresses, social security numbers, and financial details that obtain by cybercriminals in an illegal way.
- ✅ Cybercriminals obtain Fullz through data breaches and phishing scams, exploiting company databases and tricking individuals into revealing their personal information.
- ✅ The dark web serves as a marketplace for buying and selling Fullz, providing anonymity to criminals involved in illegal activities.
- ✅ Stolen Fullz can be used for identity theft, allowing criminals to assume victims’ identities and engage in fraudulent transactions, causing financial and emotional distress.
- ✅ Both individuals and businesses face serious consequences as a result of Fullz exploitation, including financial losses, damaged reputations, and potential legal liabilities.
Remember to protect your personal information, be aware of phishing attempts, and regularly monitor your accounts for any signs of unauthorized activity.
2. What are the Components of Fullz?
A typical Fullz package contains a variety of personal information that can be exploited for criminal activities. The components may include:
2.1. Full Name: The complete name of a person, including first name, middle name, and last name.
2.2. Address: The individual’s full residential address including street name, city, state, and ZIP code.
2.3. Social Security Number (SSN): A unique nine-digit identifier used for government and financial purposes. The SSN is a crucial component of Fullz, enabling identity theft and fraudulent activities.
2.4. Date of Birth (DOB): The birthdate information of the individual, which is often used as an additional identifier for various online and offline transactions.
2.5. Financial Information: This includes credit card details, bank account numbers, and other financial data that can be exploited for unauthorized transactions and fraudulent activities.
2.6. Online Account Credentials: Fullz may also contain login credentials for various online accounts, such as email, social media, or online banking. This allows cybercriminals to access and manipulate victims’ accounts.
3. How Does Fullz Work?
Obtaining Fullz involves various methods that cybercriminals employ to gain unauthorized access to personal information. Some common methods include:
3.1. Data Breaches: Large-scale security breaches on websites, online platforms, or organizations can lead to the exposure of sensitive personal data.
Cybercriminals exploit these breaches to collect Fullz.
3.2. Phishing Attacks: Phishing is a fraudulent technique where cybercriminals pose as trustworthy entities to deceive individuals into divulging their personal information.

Phishing emails or fake websites are designed to mimic legitimate sources, tricking victims into providing their Fullz.
3.3. Social Engineering: Cybercriminals may employ manipulation tactics to deceive individuals into sharing their personal information willingly.
Techniques such as pretexting, baiting, or posing as trusted individuals or organizations can lead to the acquisition of Fullz.
3.4. Insider Theft: In some cases, individuals with authorized access to personal information may misuse their privileges to collect and sell Fullz.
This can involve employees of companies or organizations with access to databases containing valuable personal data.
4. What is The Relation Between Dark Web and Fullz?
The dark web is where Fullz and other illegal goods and services are bought and sold. It’s like a secret part of the internet where people can stay anonymous.

To access the dark web, cybercriminals use special software that hides their identity. This anonymity makes it easier for them to sell stolen personal information without getting caught.

5. The Utilization of Fullz. How is Fullz Use?
Once cybercriminals acquire Fullz, they can apply various tactics to exploit the stolen information. Some common uses of Fullz include:
5.1. Identity Theft: With Fullz at their disposal, cybercriminals can assume the identity of the victim. They may open new bank accounts, apply for credit cards or loans, or engage in fraudulent activities using the stolen identity.
According to researchgate.net “The Identity Theft Resource Center (“Identity theft resource center,” 2018) reported 1.077 billion identity records have been stolen as of 2018”
5.2. Financial Fraud: Fullz provides cyber criminals with the necessary information to do unauthorized transactions using victims’ credit card details or bank accounts. The victims may suffer large financial losses as a result of this.

5.3. Account Takeovers: By utilizing Fullz containing online account credentials, cybercriminals can gain unauthorized access to victims’ accounts.
This allows them to manipulate and exploit personal and financial information stored within those accounts.
5.4. Creation of Fake Identities: Fullz can be used to fabricate entirely new identities. Cybercriminals may create fake identification documents using stolen personal information, enabling them to carry out illicit activities while evading detection.
6. How Does Fullz Impact Individuals and Businesses?
Fullz can cause serious problems for both individuals and businesses. For individuals, it can lead to financial losses, ruined credit scores, and even emotional distress.

Imagine someone using your credit card to buy expensive things without your knowledge! It can take a long time to resolve these issues and put your life back on track.
Businesses also suffer when Fullz is used for illegal activities. For Example, In 2022 T-Mobile Data Breach cost the company $ 350 million.
When customer information is stolen, businesses can face financial losses and damage to their reputation. They may also be legally responsible for not protecting customer data properly.
7. Consequences of Identity Theft.
Identity theft, often made possible through Fullz, can have long-lasting consequences. The issues caused by identity theft can be difficult to resolve and might take a lot of time. Victims may have trouble getting loans, finding a job, or even renting an apartment.

According to Proofpoint, recent statistics show that 33% of US residents have at some time in their life experienced identity theft. That is more than double the average value worldwide.
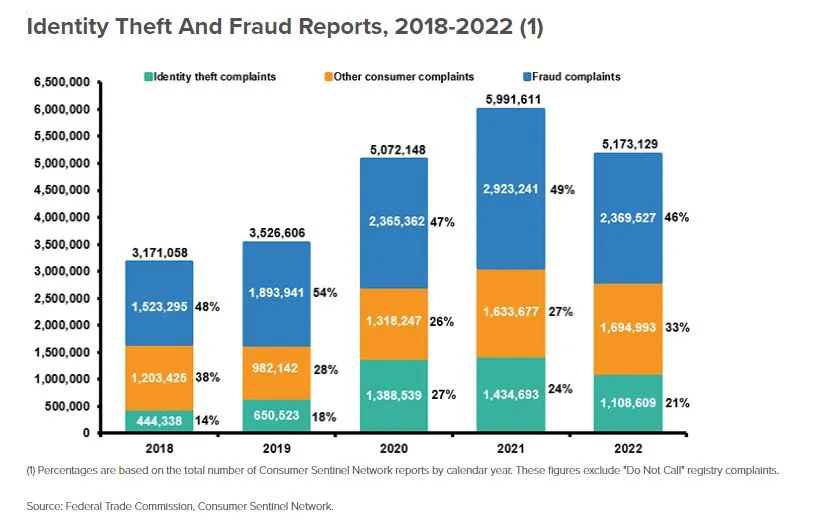
According to the Insurance Information Institute, Over 5.1 million reports were received by the Consumer Sentinel Network of the Federal Trade Commission (FTC) in 2022, of which 21% were for identity theft. That’s a staggering number! It shows how widespread and serious this problem is.
8. How to Protect Yourself from Fullz and Identity Theft.🤔
Now you understand the risks and consequences associated with Fullz, let’s talk about how you can protect yourself:
8.1. Be careful with your personal information: Only share it with trusted sources and be cautious online.
8.2. Use strong, unique passwords: Avoid using the same password for multiple accounts. Make sure your passwords are hard to guess.
8.3. Be wary of phishing scams: Don’t click on suspicious links or provide personal information through email or unknown websites.
8.4. Monitor your accounts: Regularly check your bank statements, credit reports, and online accounts for any unauthorized activity.
8.5. Use antivirus software: Use good and updated antivirus software to safeguard your gadgets from malware threats.
Remember, only awareness and caution can go a long way in keeping your personal information safe.
Conclusion
Fullz poses a serious threat to our personal and financial security. Cybercriminals are constantly trying to get your valuable information. We have provided complete information about Fullz in this article so that by understanding the risks and taking proactive steps to protect ourselves, we can reduce the chances of becoming victims of Fullz and identity theft.
Here I found a useful video from you tubes showing hows teenage fraudsters steal money using Fullz.

